mvc客户端登录验证回调异常,服务端使用Identityserver4认证

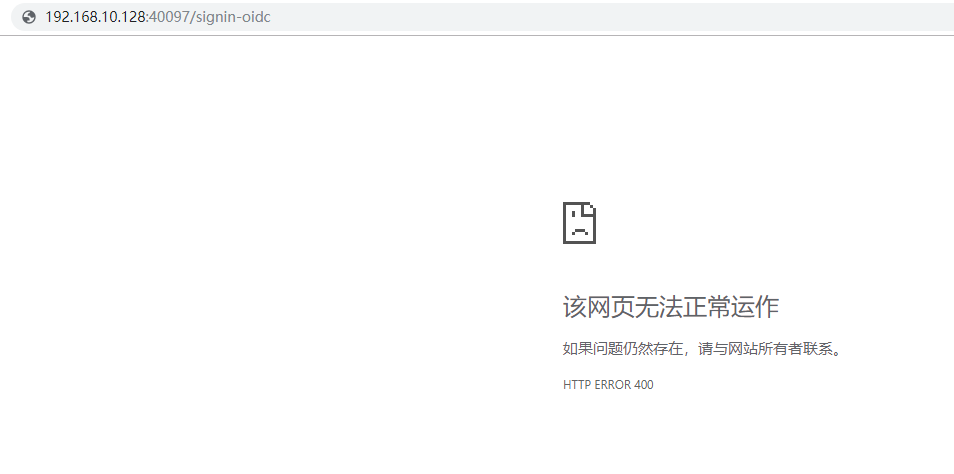
我有一个mvc客户端,使用的是混合模式认证,本地运行没有问题,但是部署到服务器以后,is4认证通过后回调,就直接跳转到/signin-oidc,提示该网页无法正常运作,如果问题仍然存在,请与网站所有者联系。HTTP ERROR 400,查看日志也没有看到错误日志输出。
以下是客户端的代码:
JwtSecurityTokenHandler.DefaultInboundClaimTypeMap.Clear(); services.AddAuthentication(options => { options.DefaultScheme = "Cookies"; options.DefaultChallengeScheme = "oidc"; }) .AddCookie("Cookies") .AddOpenIdConnect("oidc", options => { options.SignInScheme = "Cookies"; options.Authority = “http://192.168.10.100:8080”; options.RequireHttpsMetadata = false; options.ClientId = “mvc”; options.ClientSecret = "secret"; options.ResponseType = "code id_token"; options.SaveTokens = true; options.GetClaimsFromUserInfoEndpoint = true; options.Scope.Clear(); options.Scope.Add("openid"); options.Scope.Add("profile"); });
app.UseCookiePolicy(); app.UseAuthentication(); app.UseStaticFiles(); app.UseMvc(routes => { routes.MapRoute( name: "default", template: "{controller=Home}/{action=Index}/{id?}"); });
从代码上看,我也发现不了什么问题,使用同样的方法部署了多个站点,其它的都可以,就是这个不行,服务器验证成功以后,就直接跳转到http://192.168.10.133/signin-oidc, 同时出现400错误。
客户端日志:
2019-05-11 10:51:24.283 +08:00 [WRN] Using an in-memory repository. Keys will not be persisted to storage.
2019-05-11 10:51:24.402 +08:00 [WRN] Neither user profile nor HKLM registry available. Using an ephemeral key repository. Protected data will be unavailable when application exits.
2019-05-11 10:51:24.530 +08:00 [WRN] No XML encryptor configured. Key "3c666a7d-6e97-4f97-8b52-861cb03f5347" may be persisted to storage in unencrypted form.
2019-05-11 10:51:26.492 +08:00 [INF] Cookies was not authenticated. Failure message: Unprotect ticket failed
2019-05-11 10:51:27.104 +08:00 [INF] AuthenticationScheme: oidc was challenged.
is4服务器端也没有报错的日志
2019-05-11 10:51:27.022 +08:00 [DBG] Request path /.well-known/openid-configuration matched to endpoint type Discovery
2019-05-11 10:51:27.022 +08:00 [DBG] Endpoint enabled: Discovery, successfully created handler: IdentityServer4.Endpoints.DiscoveryEndpoint
2019-05-11 10:51:27.022 +08:00 [INF] Invoking IdentityServer endpoint: IdentityServer4.Endpoints.DiscoveryEndpoint for /.well-known/openid-configuration
2019-05-11 10:51:27.022 +08:00 [DBG] Start discovery request
2019-05-11 10:51:27.028 +08:00 [DBG] Found ["openid","profile","school","api1"] as all scopes in database
2019-05-11 10:51:27.078 +08:00 [DBG] Request path /.well-known/openid-configuration/jwks matched to endpoint type Discovery
2019-05-11 10:51:27.078 +08:00 [DBG] Endpoint enabled: Discovery, successfully created handler: IdentityServer4.Endpoints.DiscoveryKeyEndpoint
2019-05-11 10:51:27.078 +08:00 [INF] Invoking IdentityServer endpoint: IdentityServer4.Endpoints.DiscoveryKeyEndpoint for /.well-known/openid-configuration/jwks
2019-05-11 10:51:27.078 +08:00 [DBG] Start key discovery request
2019-05-11 10:51:27.128 +08:00 [DBG] Request path /connect/authorize matched to endpoint type Authorize
2019-05-11 10:51:27.128 +08:00 [DBG] Endpoint enabled: Authorize, successfully created handler: IdentityServer4.Endpoints.AuthorizeEndpoint
2019-05-11 10:51:27.128 +08:00 [INF] Invoking IdentityServer endpoint: IdentityServer4.Endpoints.AuthorizeEndpoint for /connect/authorize
2019-05-11 10:51:27.128 +08:00 [DBG] Start authorize request
2019-05-11 10:51:27.129 +08:00 [DBG] User in authorize request: 8cd82630f81a
2019-05-11 10:51:27.129 +08:00 [DBG] Start authorize request protocol validation
2019-05-11 10:51:27.134 +08:00 [DBG] CLIENT found in database: true
2019-05-11 10:51:27.134 +08:00 [DBG] client configuration validation for client CLIENT succeeded.
2019-05-11 10:51:27.134 +08:00 [DBG] Checking for PKCE parameters
2019-05-11 10:51:27.134 +08:00 [DBG] No PKCE used.
2019-05-11 10:51:27.136 +08:00 [DBG] Found ["openid","profile"] identity scopes in database
2019-05-11 10:51:27.141 +08:00 [DBG] Found ["api1"] API scopes in database
2019-05-11 10:51:27.142 +08:00 [DBG] Found ["openid","profile"] identity scopes in database
2019-05-11 10:51:27.146 +08:00 [DBG] Found ["api1"] API scopes in database
2019-05-11 10:51:27.146 +08:00 [DBG] Calling into custom validator: IdentityServer4.Validation.DefaultCustomAuthorizeRequestValidator
2019-05-11 10:51:27.146 +08:00 [INF] ValidatedAuthorizeRequest
{"ClientId":"CLIENT","ClientName":"CLIENT","RedirectUri":"http://192.168.10.133:8080/signin-oidc","AllowedRedirectUris":["http://192.168.10.133:8080/signin-oidc","http://localhost:29111/signin-oidc"],"SubjectId":"8cd82630f81a","ResponseType":"code id_token","ResponseMode":"form_post","GrantType":"hybrid","RequestedScopes":"systemapi pmapi basicapi offline_access openid profile","State":"4UgFIk6n4JAz_AJ1pwfbY0T57p00Dq2XlFiV3BJ6_oM649ZRVQZvSwVcft4wYrU8C3iBa8VWOoCrwTl3orAV45jjQIsQdG0sVdBtFhVHp8upsAE1waRfSu3eibU6M9_tm2m3DwG-EEqKE5h-k2fDOmYqP5cjab5SWRJtjjoDIGzjPwIReNk7lnAOquyMUtarJz_sUdC3qhyMoJvPaNmkGpoXLUxs0kIh8Efxu0S_ecIfD4N3X1hesEDtP6ScQ0lV7QmuS4BBNlvtKuPaZBP0EKnNf0cxyLORneSDX_4Y1SY8VF83JzI4Ayi0_N4","UiLocales":null,"Nonce":"636931398870976449.YjAzYmJjODEtNGVkMi00MTRiLWIwM2QtMTUyZjZjNGJmMDFkNzJlY2U5OTYtZGY3OS00ZmE3LWEyNzAtNjNiMjBmOWZiMmRl","AuthenticationContextReferenceClasses":null,"DisplayMode":null,"PromptMode":null,"MaxAge":null,"LoginHint":null,"SessionId":"2e8794e302771caf27710bb9916dbbcd","Raw":{"client_id":"CLIENT","redirect_uri":"http://192.168.10.133:8080/signin-oidc","response_type":"code id_token","scope":"systemapi pmapi basicapi offline_access openid profile","response_mode":"form_post","nonce":"636931398870976449.YjAzYmJjODEtNGVkMi00MTRiLWIwM2QtMTUyZjZjNGJmMDFkNzJlY2U5OTYtZGY3OS00ZmE3LWEyNzAtNjNiMjBmOWZiMmRl","state":"4UgFIk6n4JAz_AJ1pwfbY0T57p00Dq2XlFiV3BJ6_oM649ZRVQZvSwVcft4wYrU8C3iBa8VWOoCrwTl3orAV45jjQIsQdG0sVdBtFhVHp8upsAE1waRfSu3eibU6M9_tm2m3DwG-EEqKE5h-k2fDOmYqP5cjab5SWRJtjjoDIGzjPwIReNk7lnAOquyMUtarJz_sUdC3qhyMoJvPaNmkGpoXLUxs0kIh8Efxu0S_ecIfD4N3X1hesEDtP6ScQ0lV7QmuS4BBNlvtKuPaZBP0EKnNf0cxyLORneSDX_4Y1SY8VF83JzI4Ayi0_N4","x-client-SKU":"ID_NETSTANDARD2_0","x-client-ver":"5.3.0.0"},"$type":"AuthorizeRequestValidationLog"}
2019-05-11 10:51:27.146 +08:00 [DBG] Client is configured to not require consent, no consent is required
2019-05-11 10:51:27.146 +08:00 [DBG] Creating Hybrid Flow response.
2019-05-11 10:51:27.148 +08:00 [DBG] yTrOyFNaDGDdjoCALDkxbh46YqQstu0Kn5xz1xtdLzY= not found in database
2019-05-11 10:51:27.150 +08:00 [DBG] Creating Implicit Flow response.
2019-05-11 10:51:27.150 +08:00 [DBG] Getting claims for identity token for subject: 8cd82630f81a and client: CLIENT
2019-05-11 10:51:27.151 +08:00 [DBG] Claim types from profile service that were filtered: ["sub","idp","amr","auth_time"]
2019-05-11 10:51:27.153 +08:00 [INF] Authorize endpoint response
{"SubjectId":"8cd82630f81a","ClientId":"CLIENT","RedirectUri":"http://192.168.10.133:8080/signin-oidc","State":"4UgFIk6n4JAz_AJ1pwfbY0T57p00Dq2XlFiV3BJ6_oM649ZRVQZvSwVcft4wYrU8C3iBa8VWOoCrwTl3orAV45jjQIsQdG0sVdBtFhVHp8upsAE1waRfSu3eibU6M9_tm2m3DwG-EEqKE5h-k2fDOmYqP5cjab5SWRJtjjoDIGzjPwIReNk7lnAOquyMUtarJz_sUdC3qhyMoJvPaNmkGpoXLUxs0kIh8Efxu0S_ecIfD4N3X1hesEDtP6ScQ0lV7QmuS4BBNlvtKuPaZBP0EKnNf0cxyLORneSDX_4Y1SY8VF83JzI4Ayi0_N4","Scope":"openid profile systemapi pmapi basicapi offline_access","Error":null,"ErrorDescription":null,"$type":"AuthorizeResponseLog"}
服务器的配置问题导致
options.AuthenticationMethod = OpenIdConnectRedirectBehavior.FormPost;添加这个试试??
谢谢!!
但是还是不行,这个错误确实挺烦人的。
授权服务器里 Client实例要配置属性RequireConsent=true;
请问楼主如何解决这个问题的?
请问楼主如何解决这个问题的?
解决了吗?同问
app.UseRouting();
//***
app.UseAuthentication();
app.UseAuthorization();